Read the reason for these posts. Read Steve Gibson’s response.
Here I am again, as promised. I won’t turn soft because of a nice e-mail. (Then again I hope that these posts are of technical nature, they point out objective mistakes and don’t become a personal attack. If you think that I’m sliding in that direction, please tell me, so that hopefully I can turn around).
Because this episode is a listener Q&A episode, I’ll structure my comments also by those questions.
Regarding the first question Steve gives some very accurate an good response / advice (like not running as Administrator). I just want to add one curiosity: you can in fact temporarily deny access to the host file by the Administrator. Do the following: log in as administrator and go where the hosts file is located. Right click on it, select the security tab and check the Deny boxes. Click apply and respond yes to the two warnings (after reading them of course, I’m not advocating here the mindless clicking of message boxes :)). Now you’ll see that you can’t access your hosts file (try to open it in notepad for example). This will stop stupid malware that’s not expecting this, however it will not block malware that is smart enough to take the appropriate actions (if it’s running in an administrative account). Basically it can restore the permissions to the previous state, as can you by going again to the security tab and unchecking the deny boxes. A small piece of trivia Windows XP on x64 has a feature
called file system redirectors which can again prevent some actions of malware if it’s not expecting it (you can read more about it on Microsoft’s site, under the section Registry and file redirection
). However you shouldn’t rely on these things, and run as a normal user!
The second question sounds like it’s from someone unexperienced in the IT field (no offense) and Steve doesn’t do a good job to clean up his confusion. What he doesn’t know is that VPNs and remote desktop solutions server a fundamentally different purpose (although they can be combined). If you are using a VPN, all the applications (like Word, Excel and whatever other applications the people on the network need) run on the local, home PC and the VPN is used to access data (like shares). This indeed is a big problem is you’re worrying about data theft or malware problems (even more so if the users have write access to some shares). The other solution (remote desktop, VNC, and company) require that the applications run on a computer inside the corporate network, that is you need a computer for each user inside the corporate network (or at least a computer for each 10 or so users if you use something like Terminal Services to host multiple users on one computer). This can be more expensive and only reduces the risk of data theft voluntary (there is a feature for example in Remote Desktop – which probably can be disabled by Group Policy – using which you can mount your local drives in the remote session, meaning that even with Remote Desktop you can copy fairly easily many files) or involuntary (the users might have keyloggers installed on their computers). My advice would be: first, understand your options throughly (and consult your IT guys). Second you can take several steps to mitigate (but not eliminate – since at the end the users need some access to the data to do their jobs) the risk:
- You should require the users to have an updated security product (AV, Personal Firewall, etc) and all the security updates applied on their computer before connecting
- You should classify your users in groups if possible depending on the access s/he needs and make sure that each group has only access to the set of file they need to do their work
- If you choose to go on the VPN route, make sure that (a) they’re on a different subnet than the rest of your corporate users (b) communication between them through the VPN is disallowed (so an infected user can’t spread a worm to other users) (c) in the router you only allow communication that is needed from this subnet
- Turn on auditing on the shares you use so that you can see who did what to the files
The next question about Windows Update and limited users was very nicely answered (largely because Leo quoted an MVP who described the different scenarios), however I think Steve badmouths Microsoft without a reason. Sure windows is complex, sure there are vulnerabilities and so on, but if you know to configure it right is as secure as any other operating system. And there is a very good protection between processes, just try to use your debugger from a user account to open a system process and you’ll see the protections. The main idea is: don’t run as Administrator! (of course there are things like shatter attacks and invisible code, but they can be mitigated if applications are designed properly and you don’t run as an Administrator!).
The next question, with displaying a different error page, Leo is again right on (about running a web server on the local host). One remark though: if you insist on using IE (and lending yourself to all sorts of zero-day vulnerabilities), this page from Microsoft shows you how to customize the error page (search for Changing Error Messages
on the page). Of course there is always the option to use a resource editor on Shdocvw.dll (where the error pages are stored), but this is way simpler and you don’t have to battle with the system file protection.
Regarding the physical security, I just want to mention bump keys. Everyone worried about physical security should watch this very worrying page.
The next topic (about routers / firewalls and stuff) I’ve already covered earlier on my blog.
The next response (with regards to web servers and virtual machines) is IMHO overcomplicated. The simple answer would be: they (the local and the virtual machine) have different IP addresses, so there will be no conflict.
The next question is again related to what I already covered on my blog, however I want to add one thing: I have machines with Windows on them that I administer that are directly connected to the Internet and had no problems. Never ever! The thing is you have to know how to configure your stuff. And regarding the fact that Steve uses no firewall behind his router: defense in depth is a very good thing!
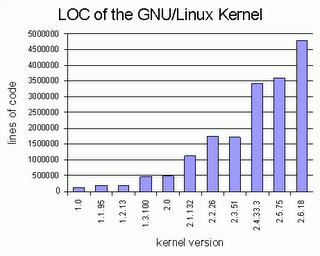
The discussion about vulnerabilities in Windows and other OSs is balanced, however the statement Linux code base has tripled made me curious, so because I’m a trust but verify
kind of huy I’ve grabbed some kernel sources and a LOC counter. Here are the results:
| Linux Kernel Version | LOC |
|---|---|
| 1.0 | 118638 |
| 1.1.95 | 195016 |
| 1.2.13 | 197721 |
| 1.3.100 | 458066 |
| 2.0 | 473608 |
| 2.1.132 | 1124033 |
| 2.2.26 | 1746754 |
| 2.3.51 | 1707055 |
| 2.4.33.3 | 3417929 |
| 2.5.75 | 3587887 |
| 2.6.18 | 4777552 |
Or if you prefer images:
An interesting sidenote: I’ve ran the line counting program on the Windows Research Kernel which I have access to through WAP, and got the value 333855. I put this number out there with the disclaimer that I have no idea which part of the system the Linux kernel source includes and which parts the WRK includes, so most probably this number is not representative at all.
Leo, about the signing of credit cards, I’ve found the following interesting links, which I think you should check out before signing your credit card (disclaimer: I don’t own / use a credit card, but the things said there make a lot of sense to me):
- To sign or not to sign?
- Should you sign the back of your credit cards?
- When You Get a New Credit Card, Should Sign on the Back (or Not?)
That’s it folks for this this episode.