We start off with a rebuttal from VMWare to a video posted by Microsoft comparing Hyper-V and VMWare ESX. While I’m no fan of any big company, such misleading marketing attempts should be considered unethical and maybe even illegal, since it contains mischaracterizations of some features like the page sharing between VMs. While in this video we clearly have a “marketing” and a “tech” guy, sometimes the “tech” guys themselves engage in such behavior: on show 52 of RunAs radio (a great, albeit somewhat Microsoft focused, IT podcast BTW) Anil Desai who is described as “an independent consultant based in Austin, TX” says something like: VMWare ESX has a large disk footprint, a couple of hundred of megabytes while Hyper-V is small, it only needs a couple of megs neglecting to mention that in order to run Hyper-V you have to have Windows Server 2008 installed which consumes a couple of Gigs.
The Braidy Tester’s blog has a very nice series entitled “Favorite Bug”. One of the recent ones was caused by a failure to strip the references to debugging symbols and the path of debugging symbols being pointed to the CD drive (on some machines). Ouch! Very obscure, very hard to reproduce and very hard to diagnose. Congratulations for catching it!
From terminal23.net: throw-away mail box sites – useful if you don’t want to receive spam like I do :-). You can get a temporary address also from PlanAHeist (via their blog).
Detecting VMware with JavaScript – the short version: it uses JavaScript to find the MAC addresses of the NIC cards and compares the manufacturer of it (the first three bytes) with the range reserved for VMWare. Of course, if you have this level of privileges from JS, you can do other things (like enumerate processes and look for the VMWare guest additions, etc). Cool idea.
Via the Reverse Engineering Reddit:
- IDC scripting a Win32.Virut variant – Part 1 – a good intro into IDA scripting.
- Bit Twiddling Hacks and The Aggregate Magic Algorithms – while they are cute and interesting to look at, never-ever use them in production code! The only exception is if you’ve profiled your code, thought about it for a week and still think that it is a good idea to do it, because understanding, debugging and porting such code can be a nightmare (also remember that “Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code as cleverly as possible, you are, by definition, not smart enough to debug it.” – Brian W. Kernighan)
- So You Want To Be a Hacker? – Part I, Part II, Part III and Part IV. It covers it from the point of view of somebody wanting to modify (“mod”) a closed-source game. Very useful to get into the mindset.
- Locked and Loaded – an error in the Windows XP SP2 exception handler (it would interesting to see exactly which versions of MS Windows exhibit this behavior)
From the fun department: Black Perl – “Black Perl is an infamous piece of Perl poetry”. Staying with the fun side of Perl, we have SuperPython (via perl one-liner). If you don’t get the joke (as I didn’t at first): it takes the number of spaces at every line, treats it like the ASCII code of a character and evaluates the resulting string. Here is how to convert a simple program to SuperPython :-).
From Scott Hanselman: Low Bandwidth View and other Hidden (and Future) Features of MSDN
From taint.org:
- Message Queue Evaluation Notes – from Second Life. Can be useful if you are looking at different options to implement MQ’s (it mainly looks at FLOSS options, which is good, both from a price and from a “debuggabiality” point of view). There is also a related comment on the Unlimited Novelty blog.
- Two sites for visualizing sorting algorithms: one more visual (with many cool options for filtering) and one static (but it might better in visually / instinctively comparing two algorithms than the first option)
- Facebook’s photo storage rewrite – very cool. Also, it is quite interesting that they found it necessary to optimize it to this level (ie. dropping filesystem structures entirely). Probably it is just the law of large numbers – the improvement might be relatively small but in absolute terms large.
- Akamai IP Application Accelerator – sounds like a cool service (routing traffic trough a private network with guaranteed characteristics), however – as the post shows – it’s not all roses and you should do a careful evaluation before using it.
- Easy AI with Python – at first I thought that he will talk about Orange or something similar, but the talks is at a much more basic level. A lot of fun. Embedded below for simplicity 🙂
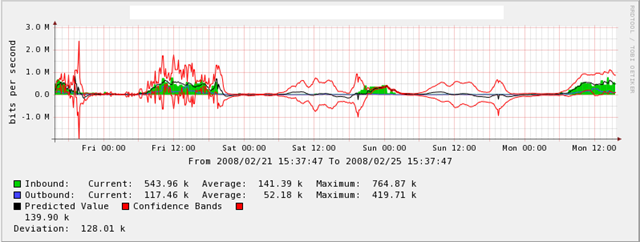
Via rootshell.be I found this page: Detecting loss of performance in Dynamic Bottleneck Capacity (DBCap) measurements using the Holt-Winters Algorithm. While it is a mouthful, it is basically a method to detect regularities in the data and predict future values based on these regularities (or more precisely: when the actual values don’t match the predicted values). It seems that rrdtool/cacti has some support for this, so you might not need to understand all the math behind for implementation 🙂 (the picture below is taken from the linked forum post).
From the SANS diary: it seems that OAuth has some serious (protocol level!) issues. This is bad, because it means that everyone (including the big boys like Google and Yahoo) who conform to the specification have this issue. Update: in the meantime they’ve released details about the problem. It is a kind of a session fixation attack, but with the OAuth session, not with the actual website session.
From the All about Linux blog: OpenOffice.org Opens up for Business – an article talking about setting up OpenOffice.org in companies. It has some good suggestions. An additional thing you could do is to set the default file format to Microsoft Word.
An interesting behavior of PHP: The Problem With is_callable() And __call()
How to grep for multiple strings: grep "string1|string2|string3" file (found it here).
From daniel.haxx.se: bittorrent vs HTTP and FTP vs HTTP – short comparisons between the different protocols. Not very detailed, but a good overview if you don’t know the details of the protocols.
Via the digitalbond blog: How to perform a full 65,535 UDP and TCP port scan with just 784 Packets – ok, the description is a little misleading, the actual mechanism is: it connects to the remote (Windows) machine trough WMI (so it must have a valid login credential) and asks for the list of open ports. Even if we abstract away from these restrictions, it’s still less accurate than a full scan, because local rootkits can subvert the system to hide open ports, which makes me question the accurateness of the phrase “If you have a PCI requirement to perform a full port scan of a target, this credentialed technique can also be used” (then again, rootkits are mostly used to hide outgoing not incoming traffic).
On the Dark Operator blog there is a nice overview of FOCA, a tool to extract metadata from a large amount of different fileformats. This can be very useful for penetration testers for example.
Via the 1raindrop blog: 10 easy steps to writing the scariest cyberwarfare article ever. Very true. I also liked the first comment:
Any insider in any walk of life could write a similar article about how the mainstream media misleads people about their specialty. The lesson is simple. The mainstream media only knows how to write a few types of stories. They will make any subject fit into one of their templates.
The funny part is that, knowing that the media doesn’t get their area of expertise right, people still believe what the media writes in areas outside of their specialty. OK, it’s not that funny. Still, I have to admire the media for their ability to write the same few stories over and over and keep people reading them.
Via the Secure Home Networks blog: an additional source for domain names to block (from emerging threats). These kinds of blacklists (although they can’t cover 100% of the problems) are very effective these days, when almost all malware tries to communicate with specific set of IPs / domain names.
From the Mu Dynamics Research Labs: Google Code respects the mime type when serving up files directly from the SVN repo. A little known feature of SVN being handy (maybe I can use this repo to host the small amount of files which will be removed from the Google Pages site) Speaking of Google Code, they added support for Mercurial, and provide a nice visualization to understand the relation between the patches.
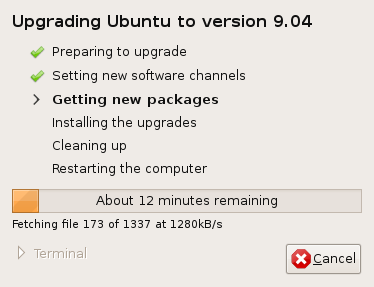
Matt Cutts managed to boot Ubuntu 9.04 in 7.83 seconds with a SSD. I myself updated to the final release yesterday and it went smoothly. The new theme is simpler and darker than the old one, which should make some people happy. And also note the number of packages it needed to download for the update:
Leet! :-). Some related notes: you can do a sudo apt-get autoremove followed by sudo apt-get autoclean to free up some space after the update. Also, VirtualBox doesn’t seem to detect that there is a new version (2.2.0) out there, you have to manually go to the site, download the new package, remove the old one and install the new. 9.04 doesn’t include the old, closed-source flgrx driver, but it actually seems to work better with the open source ones. It also includes a “cleanup” tool, but be vary that it marks manually installed packages (like VirtualBox or Opera) as “not needed”.
From Andy Helsby’s Bookmarks:
From LinuxWorld we have: 10 Expert Ubuntu Tricks – there are some nice ones in there which you might or might not have known about. For example 3, 4 and 5 were new to me.
Via the Farfromr00tin blog we have a paper about the ramifications of IE7/IE8 zones [PDF]. The gist of it: if one of your intranet sites gets powned, it is really, really bad. On a related note: Google Chrome just fixed a vulnerability related to the existence of an “undefined” zone, which made the same-origin policy exploitable.
Data escaping madness from Joshua Drake’s blog. These are small details which can bite you in the rear end, so test, test, test religiously. And also, test for failure, to make sure that the proper exception is thrown is something goes south.
Via Roger’s Security Blog: Cost of a Lost Laptop – useful is you need to convince people that laptops need additional security.
Free networking tools:
- via the FIT blog: free GFI Languard for 5 IP addresses – sounds cool, something you can experiment with on your local LAN (I never used it, so I don’t know how it measures up to something like Nessus without the professional feed)
- from Daryl Hunter: Solarwinds free IP Address Tracker – a tool which might be useful for sysadmins to keep track of assets (and investigate new / suspicious IPs)
From the carnal0wnage blog: How do YOU defend against 0day?! – the short answer: by diversifying (not using what the mainstream uses). The long answer: a large number (90%+ – I’m pulling this out of my rear-end) of computers are not even patched relative to the known vulnerabilities, so it is very rare that you have to worry about 0days.
From Arbor Networks: Many Days of DDoS for Everyone – as it stands now, there are a whole lot of people out there who can take down a whole lot of websites via DDoS, producing real financial harm for those individuals / companies (although we could debate on a philosophical level if money is real :-)). What are we going to do about it? (sidenote: every time I hear about twitter, I wonder if the people who invested all that money into it understand that 16 year old can take it offline for weeks).
Trooper.ro – a great Romanian metal band, and they’ve put many of their songs online for free. You can start here, with one of their first and maybe best known pieces.
Upcoming PHP 5.3 features and beyond – also includes a presentation of some of the PHP 6 features, mainly focused internationalization and localization (two hard problems).
One response to “Mixed links”
Nice collection.