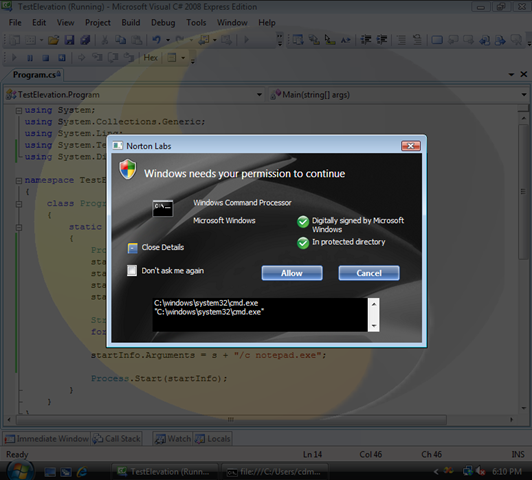
Some time ago I written about that that information given by the UAC prompt in Windows (Vista and 7) is insufficient to make the correct decision, even if we would suppose (ad absurdum) that the user knew what s/he was doing. Symantec has a research project which can be used to replace the standard UAC prompt and is supposed to give more information. However, you can still produce a very convincing dialog:
As you can see, the executable is signed by Microsoft and it is in a “protected” directory. So what’s the catch? Well, the catch is that the command line actually looks like this:
c:\windows\system32\cmd.exe ... 1000 instances of newline ...
-c notepad.exe
Of course instead of notepad.exe we could have used me_evil_program.exe. There is no visual indication of the fact that there is more information available in the textbox. In fact, the disabled scrollbars (when there is no more information available) and the active scrollbars (for the case at hand) look visually identical until you mouse over them.
So what does this mean? Prompting the user is the worst thing you can do, because it is very hard for a s/he to distinguish between information from different sources and ascertain which one can be trusted and which one can’t (an other classical example is a webpages which display the SSL lock in the webpage, yet users still think that it is as trustworthy as displaying it in the browser chrome).
Teaser: in an upcoming post I will be discussing how the concessions made by Microsoft in Windows 7 to the “UAC is annoying” crowd makes the default accounts on it virtually no more secure than the default administrator accounts created created by Windows XP during installation (hint).